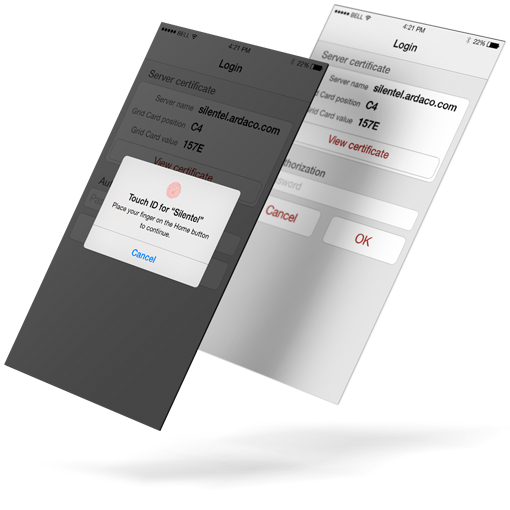
Touch ID functionality provides most comfortable way of connecting to Silentel
Standard passwords are always doubted – long and complex password provides high security but it takes time to get access to your sensitive data. Short password is fast to type but is it secure enough? Connecting to Silentel with Touch ID is quick and comfortable without losing your security.
Touch ID is supported on iPhone 5S and later with iOS 8 and later.
Touch ID login
Your fingerprint can be used to log in to Silentel. It’s not necessary to type your password. Just place your fingerprint on Home button and authentication is done in a second.
In case your fingerprint is not available (Touch ID sensor is not working, injury, etc.) you can always use your password.

Two-factor authentication after logout
What is two-factor (2FA) authentication?
Two-factor authentication provides unambiguous identification of users by means of the combination of two different components. These components may be something that the user knows, something that the user possesses or something that is inseparable from the user.
Source: www.wikipedia.org
Silentel allows you to enable 2FA to increase authentication security. When connecting to Silentel, you’re required to authenticate using your fingerprint (something you possesses) and your password (something you know).
2FA is used only for login after you log out yourself from Silentel. In case Silentel is disconnected by system, Silentel requires only your fingerprint (without password) to simplify process of re-connecting.
Touch ID app lock
Silentel allows you to enable application lock when in background. Locked Silentel can be simply unlocked using your fingerprint.
When Silentel is locked, you can answer incoming Silentel calls but access to your contacts, messages, files and other sensitive content is protected.


