Secure communications is a complex, multifaceted issue. We've spoken in length about the software side of things, such as chat apps and viruses. However, we've yet to address the hardware. That changes today.
If you value your privacy or work in an environment that's serious about confidentiality, you may have heard the term secure phone. Historically, it described landlines that enabled secure communication via end-to-end encryption.
Nowadays, the technology has been made largely obsolete by VoIP (Voice over Internet Protocol) solutions such as Silentel, Signal, Threema, and others. Nevertheless, several companies still offer secure mobile phones, primarily for use in government institutions, especially in military and tactical communications.
In this article, we seek to explain the current reality of secure phones and assess whether they have a place in modern times.
The Pitch
So far, we've discussed modern secure phones only very vaguely, so let's take a closer look at them. Although the details are always slightly different, most producers promise the following features:
- proprietary OS (Operating System)
- secure, tamper-proof hard drive
- OS integrity checks
- tamper detection
- disc encryption
- secure boot
The combination of these protective and preventive tools is supposed to create a near-perfect, impenetrable device that can withstand all potential attempts at data theft.
But what's the reality?
The Comparison
That sounds convincing, but there's a little catch. Every feature listed is also included on most middle-to-high-end Apple and Android phones. Moreover, secure mobile phones also suffer from several disadvantages that their traditional counterparts don't experience.
We'll discuss these in more detail later, but first, let's compare the standard capabilities of Apple, Android, and Proprietary Secure Mobile Phones.
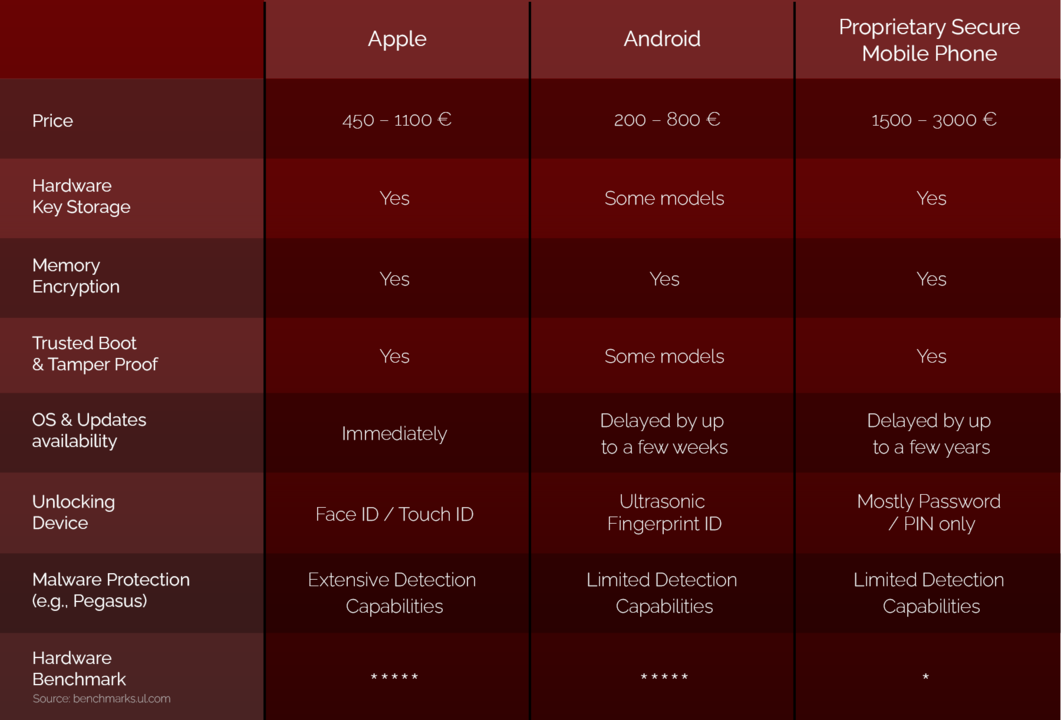
Without getting too much into the technical details, there are several issues to be discussed. These are the price point, hardware, OS and updates, and malware protection.
1. Price Point
Since the proprietary secure mobile phones are assembled in limited batches by smaller companies and claim to feature as big a list of advantages, their price point is higher. However, as shown in the table above, both Apple and Android phones offer a comparable, if not better, set of tools for a lower price.
Furthermore, secure mobile phones are rarely stand-alone, even at their price point. Most providers offer a wide selection of additional digital solutions to help you protect yourself further. Sometimes, this software is downright necessary, raising the total price even more. [1]
2. Hardware
Proprietary secure mobile phones tend to boast “hardened” and “hacker-resistant” designs. However, the truth is that most base themselves on standard Android models. So, even though they may be physically altered to provide better protection against impacts and physical stress, they can't fully protect from hands-on hacking.
If a potential data thief manages to identify the underlying model your secure phone is based on, they'll most likely be able to use known hardware exploits to get to your information.
3. OS and Updates
Despite citing a “custom-built” OS, most proprietary secure mobile phones base their operating systems on the Android platform. As such, they are subject to the same problems standard Android is. However, secure mobile phones have the added disadvantage that they are typically far behind their competitors in terms of updates.
Apple rolls out updates immediately and claims that 75% - 85% of its devices are up-to-date worldwide at any given time. Android releases updates in batches for various devices, meaning it takes a few weeks to several months for all devices to be updated.
Finally, proprietary secure mobile phone updates are slowed significantly by their custom code and limited human resources. This leads to updates being released with an average 1-2 year delay. Often, users end up with devices that are no longer supported and find themselves unable to use the latest apps and tools.
4. Malware Protection
As we discussed in our previous article, Clipping Pegasus' Wings, modern viruses typically rely on two types of attacks or exploits:
- Spear-fishing: The hacker sends their victim a compromised link or document, which, when clicked, downloads and installs the spyware in the background.
- Zero-day exploit: The hacker delivers harmful code via a vulnerability in an app that the developer is unaware of.
The human element on the victim's side and the unpredictability of these attacks make them impossible to predict and reliably prevent. So to mitigate the threat as much as possible, devices require sophisticated malware detection capabilities.
These are by far the best on Apple phones, which offer a wide selection of activity logging options. Android has several well-known vulnerabilities, making effective threat detection harder. Of course, secure mobile phones based on the Android platform also tend to suffer from the same issue.
The Reality
Taking the above-mentioned details into consideration, it's hard to wholeheartedly recommend proprietary secure mobile phones, safe for a few special situations. That's not to say you'll mess anything up by deploying them in your organization, but it's worth considering whether you can excuse the considerable price tag despite all their drawbacks.
Traditional Apple and Android phones offer comparable, if not better, malware protection, provide a better user experience, and do so at a lower cost. But say you're still concerned about your private conversations – what do you do then?
Instead of spending a fortune on an over-priced solution, consider getting a standard mid-to-high-end phone and supplementing it with a quality, secure communications app.
Silentel can offer you the same reliable level of high security across multiple devices and operating systems, including iOS, Android, and even other proprietary platforms. Our solution is used worldwide by private individuals, corporations, and governments. And for a good reason.
So, to answer our original question – Do secure mobile phones have a place in today's tech ecosystem? Yes, albeit only a limited one. Most people, be they private individuals, businessmen, or politicians, will benefit more from a combination of a good phone and quality software.
If you want to learn more about why that is, consider reading How Governments Can Protect Their Sensitive Information with an App.