Researchers have created a device that can sniff out controversial cell phone surveillance devices, known as IMSI-catchers or StingRays (commercial IMSI catcher from Harris Corporation), used by federal and state law enforcement as well as hackers.
StingRays are used by a dozen federal agencies, including the FBI, NSA, DEA, the Immigration and Customs Enforcement agency and all branches of the US military. But researchers identified at least 48 other agencies in the US that use StingRays illegally.
The increased use of IMSI-catchers makes it increasingly important that IT security managers look at the secure mobile communications (SMC) and mobile threat defense (MTD) technology market, the products available and how they should be used, according to Gartner.
Read the full article about university research to detect illegal IMSI catchers:
Computerworld:
Rogue cell phone surveillance gives rise to mobile threat defense
What’s an IMSI catcher?
IMSI-catchers work by pretending to be a legitimate cell tower that a smartphone would typically use. The catchers trick the cell phone into sending identifying information about its location and how it is communicating.
How do IMSI catchers work?
The IMSI-catchers have not only been used to locate mobile devices but also to intercept and eavesdrop on users’ data and communication.
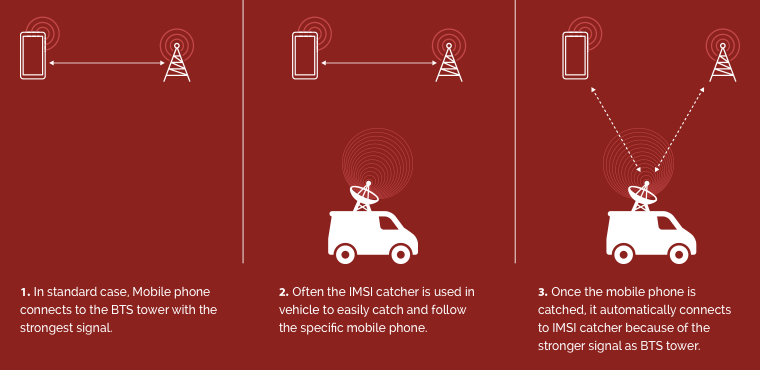
Law enforcement officials but also hackers are using surveillance devices quietly. When IMSI catcher is on, it’s not possible to detect that your mobile phone is traced.
How much do IMSI catchers costs?
The portable surveillance devices range in size from a walkie-talkie to a suitcase and in price from a few thousands to hundreds of thousands of dollars.
There’re many manuals on the internet on how to assemble an IMSI catcher using off-the-shelf components under thousand dollars.
Live mobile phone spying using IMSI catcher built with components under thousand dollars
What to do and how to protect your privacy?
To protect against IMSI catchers is quite easy (similar for SS7 vulnerabilities). All you need to do is to use any VoIP (voice-over internet) encryption application instead of standard voice and SMS services provided by a mobile operator. In this case, an IMSI catcher will intercept only encrypted data.
For this purpose, you can use applications like WhatsApp, Telegram, Signal and similar. However, these applications have other security vulnerabilities. To reliably protect your privacy against wiretapping and interception it is advised to use Silentel.

